
GoPhish Nginx Reverse Proxy for Beginners
Gophish is an open-source phishing framework that enables penetration testers to conduct simulated phishing attacks to assess the security awareness of an organization’s employees. Its

Gophish is an open-source phishing framework that enables penetration testers to conduct simulated phishing attacks to assess the security awareness of an organization’s employees. Its

Welcome to the inaugural blog post for our Tool Tuesday! On the first Tuesday of each month one of our penetration testers will share a

Author: Adam Pawloski Happy New Year everyone! I’ve recently passed the exams for the Offensive Security Experienced Penetration Tester (OSEP) and Certified Red Team Operator

We see it all the time, you go to renew your cyber insurance policy or apply for new converage and the carrier gives you a

Physical devices are cool and all, but how cool would it be to create virtual mobile infrastructure and install mobile applications on it. Better yet,
A few years back, the concept of red teaming was all the rage and at the tip of the tongue of every information security professional.

I’ve had a lot of people emailing us asking for some of our common command usage for internal penetration testing engagements. This is a list

Zoom has been under the gun in recent weeks due to “cyberattacks” such as “zoom bombing”. Users have been flocking to alternative video conferencing solutions
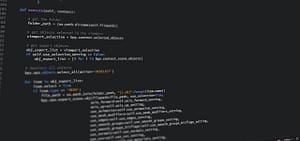
One of the articles that I have written that got the most traction was the one regarding exploiting MS17-010 with Metasploit back in 2017. Well,
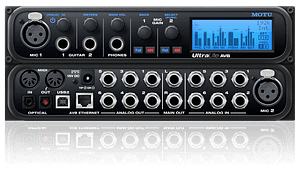
We’ve found that MOTU AVB devices contain a directory traversal vulnerability. During testing, we were able to append characters to the end of the URL

The exploit frameworks have come and go over the years. Meterpreter was excellent, easy, and effective (and actually still works on a lot of networks
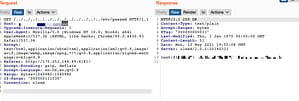
SpecoWeb (presumably all versions or at least all versions that I have tested) is vulnerable to a directory traversal vulnerability. This vulnerability can be exploited