As a penetration tester, you’ll frequently encounter client networks using sophisticated endpoint detection and response (EDR) solutions that can derail your efforts. Gone are the days when you could simply run a basic payload, establish a command and control (C2) session, extract administrator credentials, and move on. Commercial EDRs have grown remarkably stronger over the past 5 years—even Microsoft Defender has made significant strides. This is particularly true for industry leaders like Crowdstrike, SentinelOne, and Sophos. Researching and bypassing these solutions independently requires substantial time and determination from penetration testers and red teamers. At Hacket, we can’t dedicate extensive time to bypassing these solutions during engagements. Nevertheless, we still need to demonstrate potential compromise risks to our clients by circumventing these defenses. To address this challenge, we’ve found our solution in the “Balliskit” toolkit.
Balliskit is an automated toolkit that generates payloads equipped with cutting-edge evasion techniques. These techniques help create payloads that can bypass top-tier endpoint solutions during red team and penetration test engagements. When you purchase a license from the Balliskit team at balliskit.com, you get access to two tools: Shellcode pack and MacroPack Pro. MacroPack Pro creates payloads for Microsoft applications like Word, PowerPoint, and Excel. Shellcode pack handles Windows binaries such as EXEs, DLLs, and source-code scripts. For this blog, we’ll focus on Shellcode pack.
For this demo, I’m using Cobalt Strike on an AWS instance and a Windows device running SentinelOne. After setting up Shellcode pack, you can launch its user-friendly GUI. The input file is the raw .bin file created by your C2—in this case, a standard bin file from Cobalt Strike.

Select x64 for the architecture to match our victim device. The output folder defaults to your Shellcodepack installation location, though you can specify a custom folder for payloads. From the format drop-down menu, choose your desired binary type (.exe or .dll)—we’ll create an executable (.exe) for this demo. The Container option lets you package the .exe within another file like a ZIP or TAR, which can help with initial bypass. We’ll skip the Container option for this demonstration and simply name our file s1bp.exe before clicking next in the bottom right.
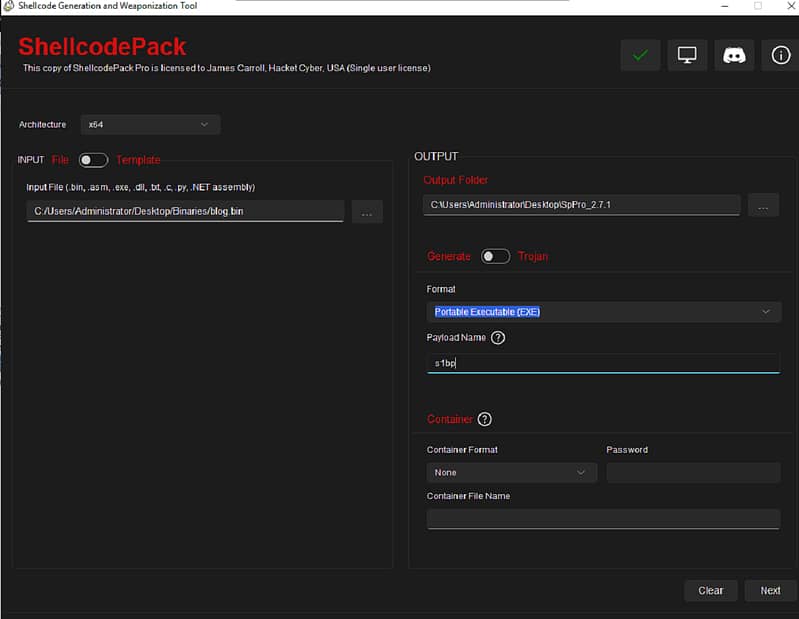
The next page displays bypass profiles at the top. This is one of Balliskit’s best features, as it lets you customize your bypass specifically for your target EDR. While there are numerous options available, for this demo we’ll select the S1 (SentinelOne) option.
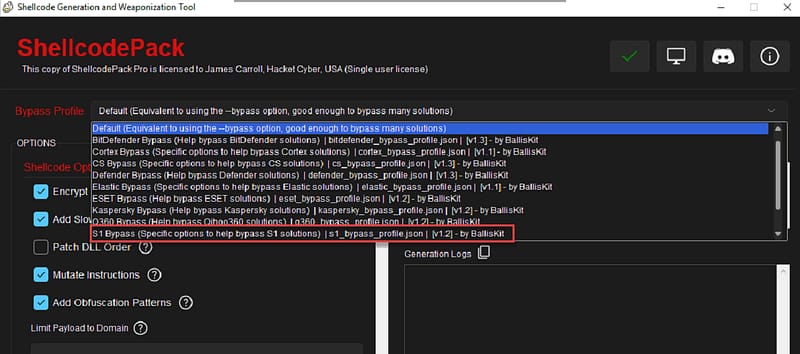
After selecting a profile, you’ll see the command-line version showing the flags and modes being used. This view helps you understand the payload’s configuration and is particularly useful if you need to run Balliskit via command line. The left panel displays the flags and modes selected for your chosen profile. While it’s best to leave these settings unchanged at first, if your payload gets blocked, you can experiment with various options to improve its success rate.
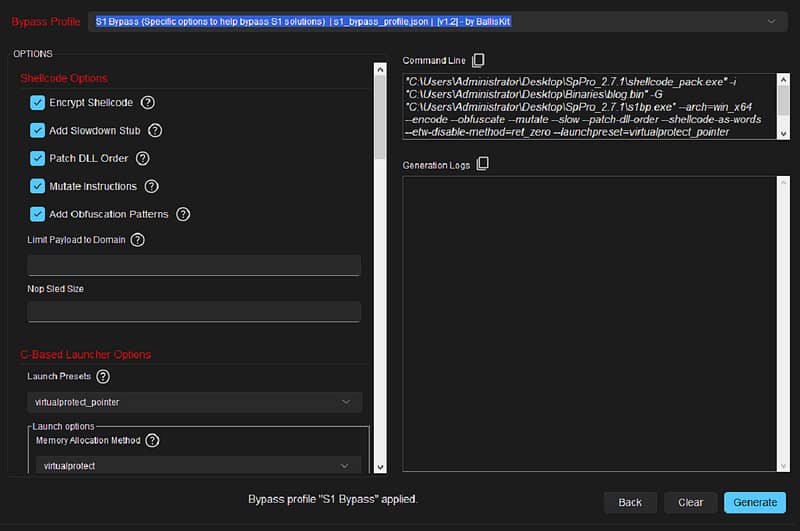
When you’re satisfied with your settings, click “Generate” in the bottom right corner. The payload creation process takes just a few seconds.

The payload is now ready for transport to your testing environment. For this demo, I’m using a Windows device equipped with SentinelOne. After transferring and executing the .exe, I successfully establish an administrator beacon on the device. I run a basic getuid command to display the username—though be aware that certain actions like attempting to extract credentials with mimikatz may terminate your beacon.

I checked my local SentinelOne instance and confirmed that the payload wasn’t detected, quarantined, or blocked. However, this could change depending on what commands you execute through the beacon—so be sure to establish persistence during your engagements!

Written by Adam Pawloski – Senior Penetration Tester
Februrary 20th, 2025



