Zoom has been under the gun in recent weeks due to “cyberattacks” such as “zoom bombing”. Users have been flocking to alternative video conferencing solutions such as Microsoft Teams, WebEx, GoToMeeting, amongst others. I’m not going to go in depth here because these has been beaten to death by the media and I’m assuming if you made it this far you know how to use google and find those articles that have been reposted by every “information security professional” in existence.
What people don’t realize is that the problem is not a Zoom issue, it’s an Meeting ID issue and more importantly a user issue. Now let’s take a journey and explore not just Zoom but ALL of the video conferencing applications out there for some fun. Other infosec aficionados may have titled this “Conference Bombing for Fun and Profit” which could make some sense here 🙂 .
Zoom Bombing
We’ll start with what the media has been dubbing as “Zoom Bombing” amongst other silly names. The attack is quite simple. If you take any Zoom meeting out of a calendar, they all have the same “prefix” and are appended with a number being the Meeting ID for said meeting. These are 9 character meeting ID’s and, when a user navigates to it, it will present them options to join the conference. They normally look like https://zoom.us/j/123456789.
Note that /j/ after zoom.us, which probably stands for “join” although I have not seen any official documentation on that 😄 . This will be important in the next step.
Now, all a person would have to do is “guess” a Meeting ID number, throw that number in their URL and they can join a meeting, right? Well, yeah, that is right, and that’s in essence what “Zoom Bombing” is. The issue is that people have been posting videos and images of their Zoom meetings, and at the top of that meeting shows the ID. Now, all you have to do is type https://zoom.us/j/<<someID>> and you’ll probably join right in. So can we automate this without searching through instagram screenshots?
AlienVault has a neat service called Open Threat Exchange (OTX) where security professionals can sign up and share some intel on threats they have been seeing, malicious URL’s, etc. I’m not entirely sure how Zoom URL’s and oodles of other benign URL’s make their way into that platform, but they do (I’m presuming it’s because of a cloud service being blocked by some configurations and then it gets thrown in the OTX). We can search against this database using some pretty cool scripts.
One is a nice little script written in GO called GetAllURLs (gau) and can be found on GitHub here https://github.com/lc/gau. This allows us to search against the OTX via command line and pass it to some of other native Linux tools for quick parsing and data retrieval. Now that we have this tool installed and cloned onto our Kali machine, let’s make a nice query. Note that this query was stolen from @nullenc0de’s twitter who is a brilliant researcher and also a friend of mine (https://twitter.com/nullenc0de)
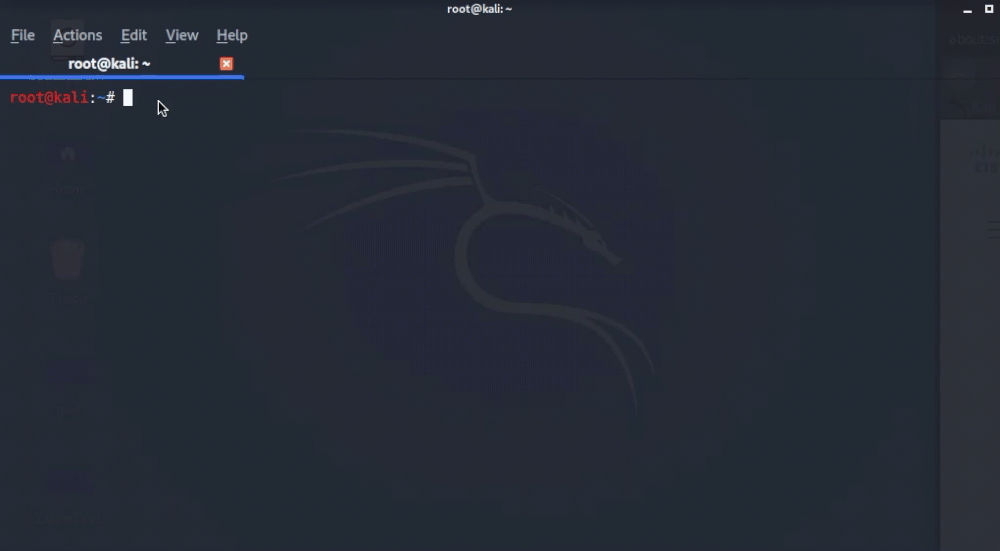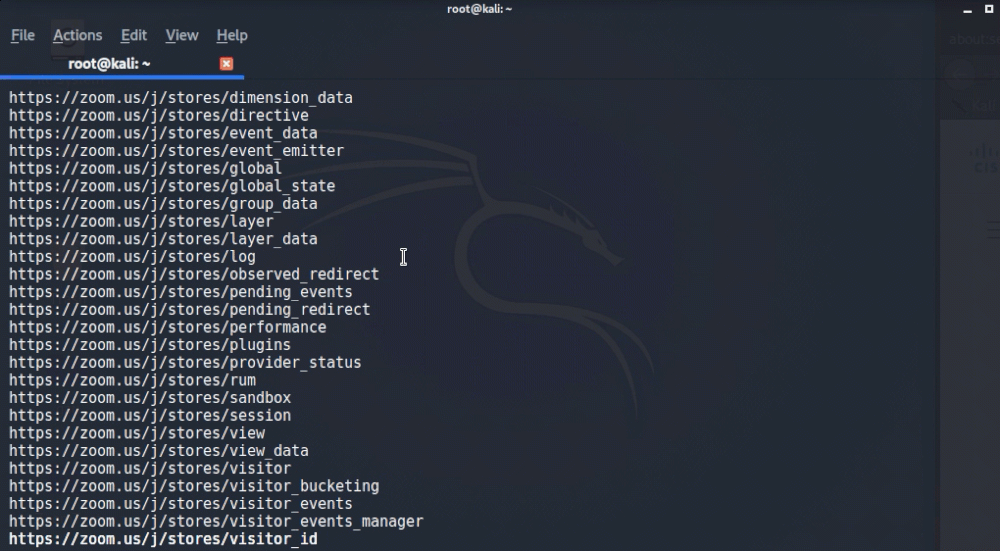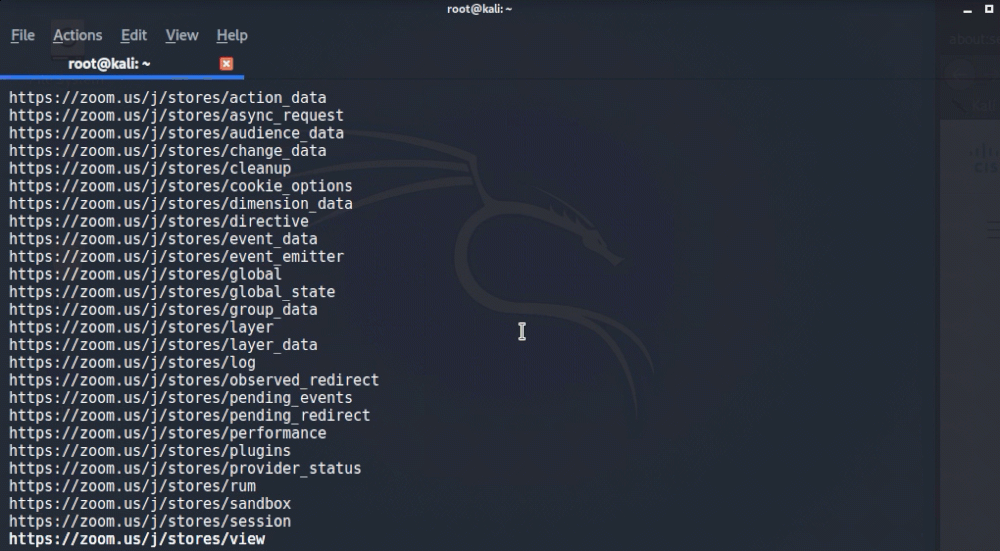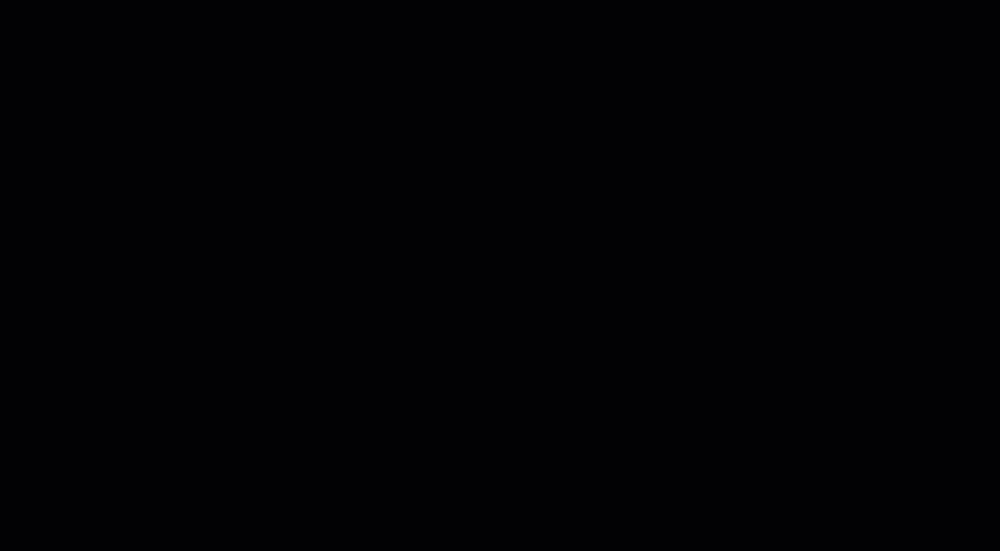
We can run that again with the > zoomurls.txt and now we have a huge list of potential Zoom meetings that we can join! How marvelous. There’s a handful of ways that you can mass open those url’s (the one that comes to mind is firefox $(cat zoomurls.txt) but you better have some serious computing power to have it rip through that list), but that’s a little out of scope for what we’re after here. I just picked one random Zoom meeting out of the list and attempted to join, and what do you know, I’m waiting for the host to start the meeting. Looks like it worked!
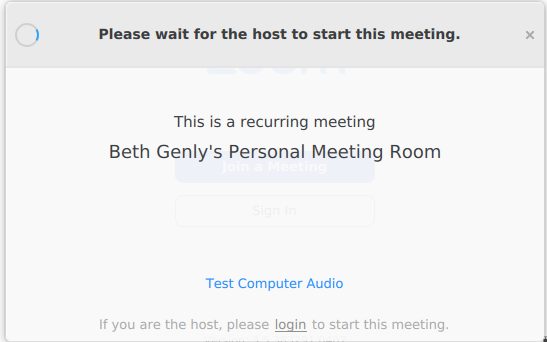
So we did it, we did our first “Zoom Bomb!”. You are now amongst some of the elitist hackers in the world and the world should flee from Zoom to other platforms because of these security atrocities. Fortunately, both of those statements are false.
WebEx Bombing
Let’s take our methodology above and apply it to another video conferencing platform that isn’t making headlines, such as Cisco WebEx. We’ll need to know what WebEx joining URL’s usually look like. Fortunately looking at some of your past calendar meetings will surely have an example of this. After examining one, we’ve determined that the URL’s usually look like the following.
companyname.webex.com/company/g.php?MTID=meetingid
The above example is a bit more “complex” than the Zoom one, but the attack scenario is almost identical. We’ll use the same tool as before but with a couple different options. The usage for this one will look like the following.
Echo Webex.com | gau.go -subs | grep “MTID=“
This will tell gau to query OTX for findings for Webex.com with MTID in the URL and will also have it query for subdirectories. This is important because, as we have illustrated from prior calendar invites, the subdirectory is commonly the companies name that is using Webex. Using this ,we get oodles of findings!
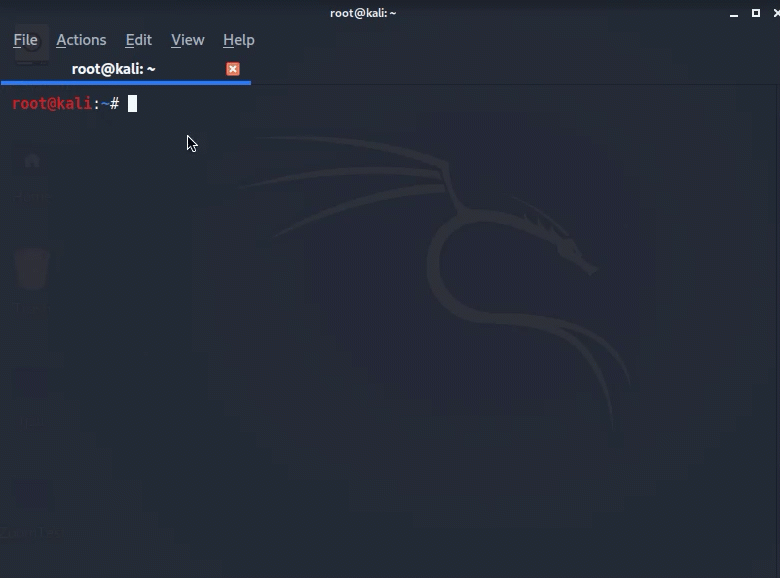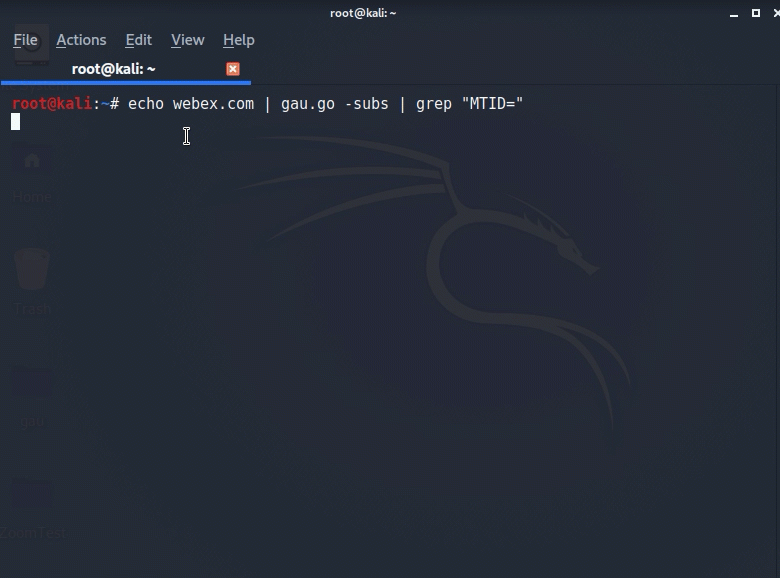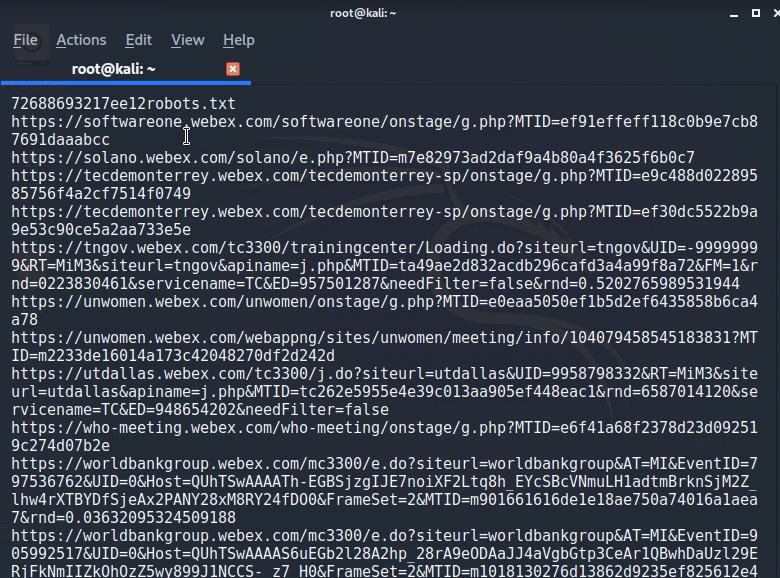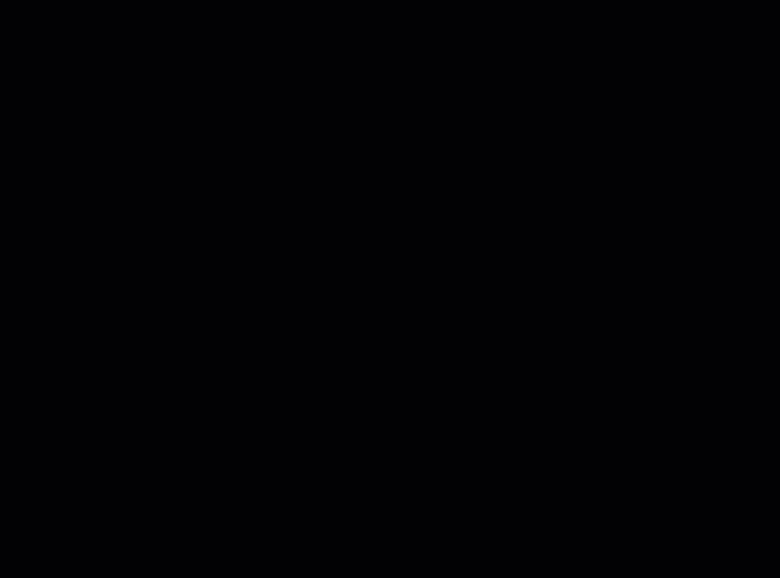
Now let’s look through these results. Their can’t possibly be meeting ID’s in there that could let us “hijack” or “join” these meetings like the infamous Zoom? That would be ludicrous!
But…there is. And there’s lots of them. Case in point.

I know what you’re thinking, you’ve been lied to. And you’ve convinced the CFO to buy hundreds WebEx license to avoid this and amidst the pandemic he initially gave you some flak, you showed him all these scary “Zoom Bombing” articles and he caved. Well, I’m presuming you won’t be showing him this 🙂 .
Note that in response to these types of attacks, Zoom has made it so that request has to be granted to share a screen (in the past any person in the video call could start sharing their screen without any input on the hosts behalf.
GoToMeeting Bombing
At this point we don’t need to do a whole lot of explaining, just show what the meeting URL’s look like and what that can do. For GoToMeeting, the URL’s look like the following.
Let’s do our thing.
Echo global.gotomeeting.com | gau.go | grep “/join/“
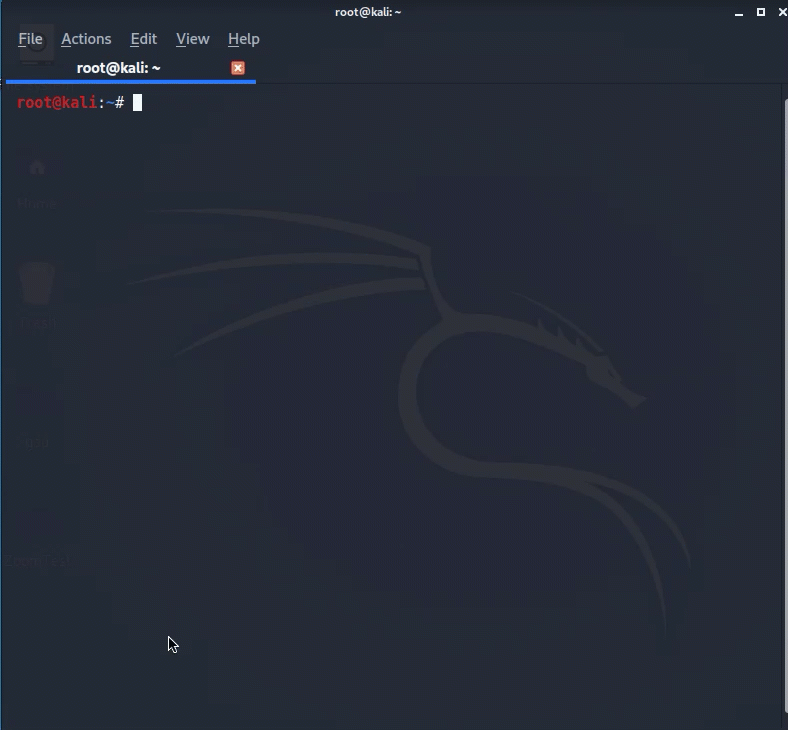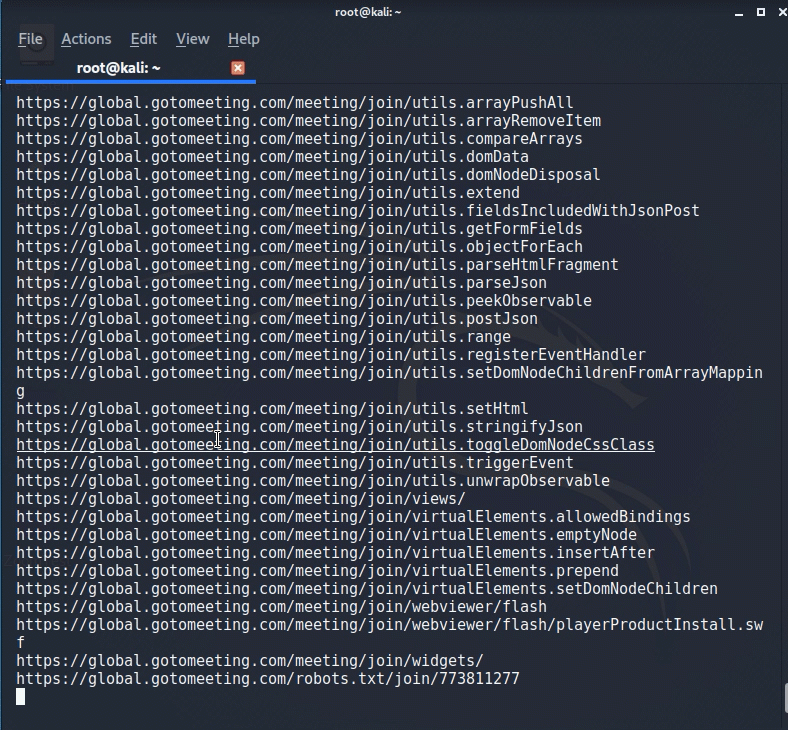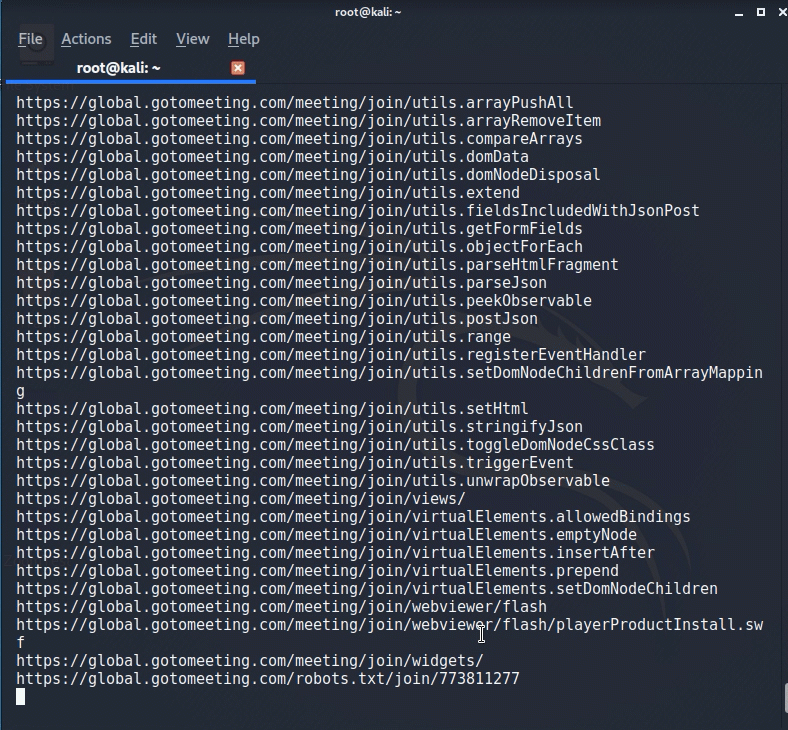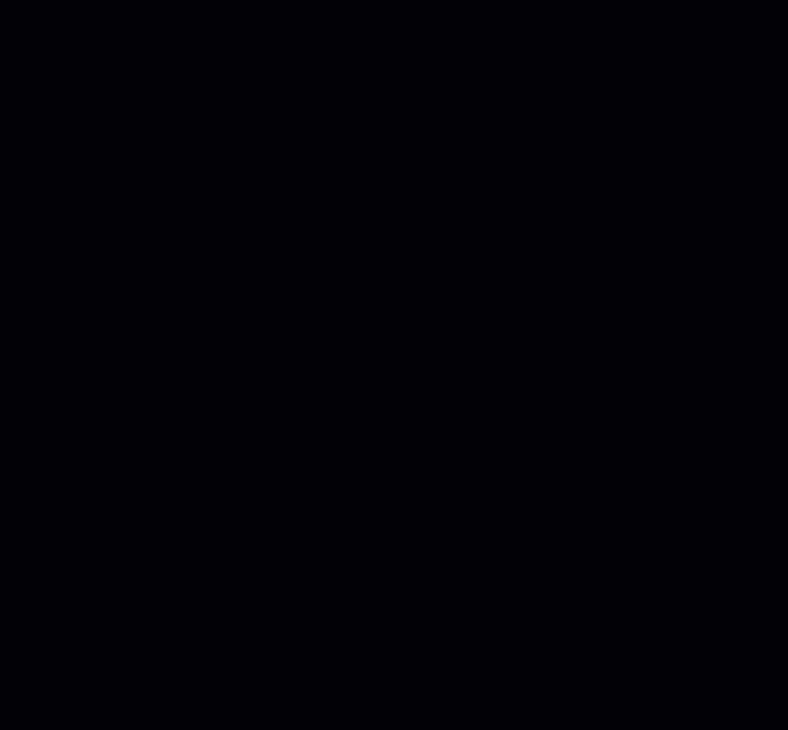
And finally our example that some of these URL’s will allow us to join.

Microsoft Teams Bombing
Teams has the strangest of URL’s, but it can still be accomplished. The look something like:
Let’s try our luck.
Echo https://teams.microsoft.com | gau.go | grep “/l/meetup-join/”
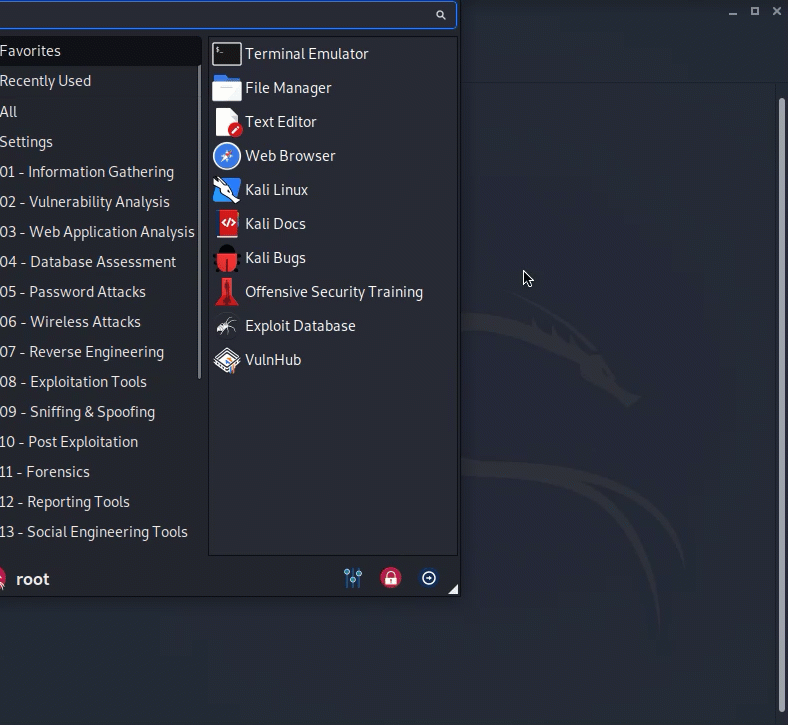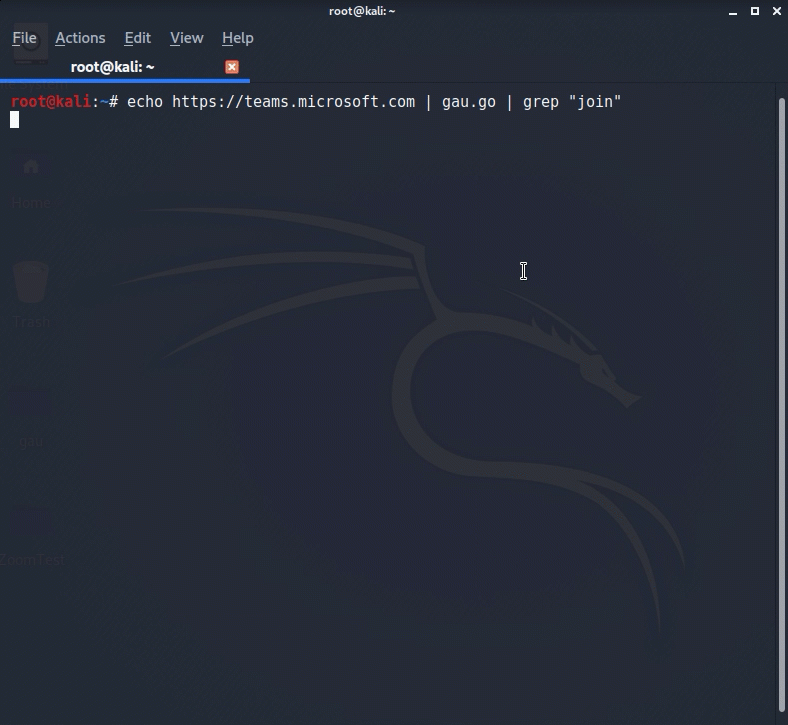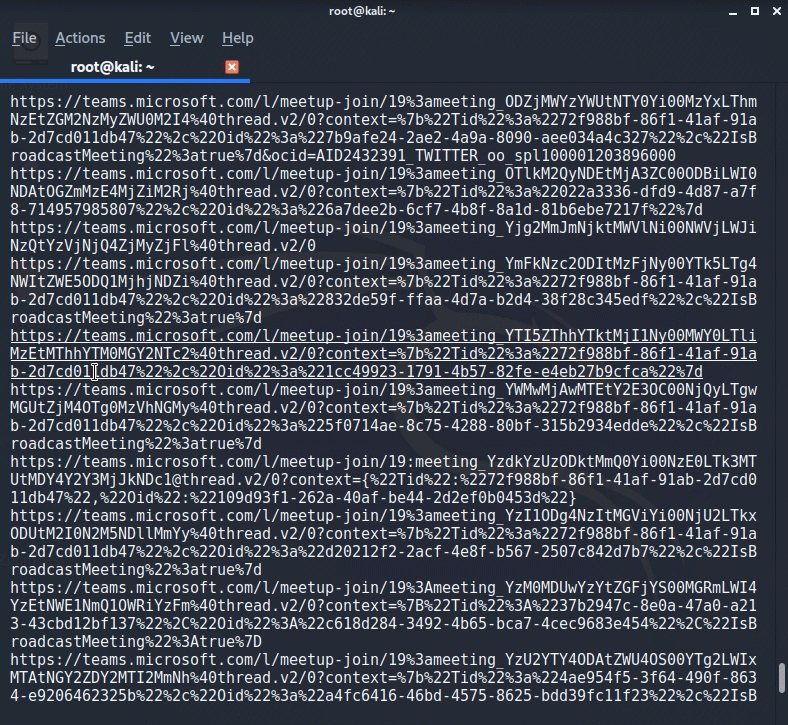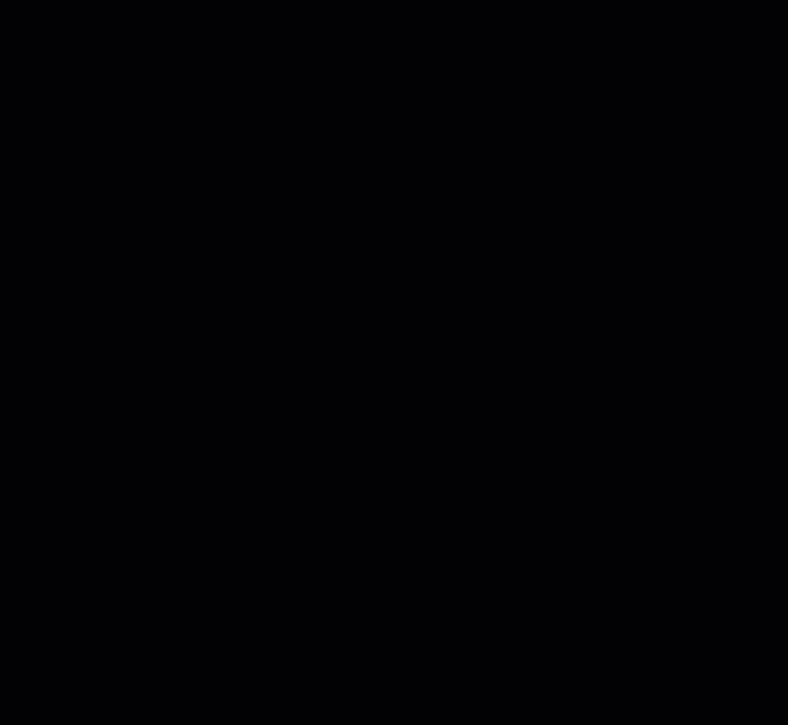
And proof that I’m not a liar.

Conclusion
As tons of other media outlet are reporting, to avoid these bombing attacks use best practices regardless of what product you are using. These include
- Enable a waiting room and manually approve guests.
- Enable a password for meetings that need to be entered by the participants.
- Avoid re-using Meeting ID’s (I know this varies per solution).
- Have fun and put your pet on the video call.



